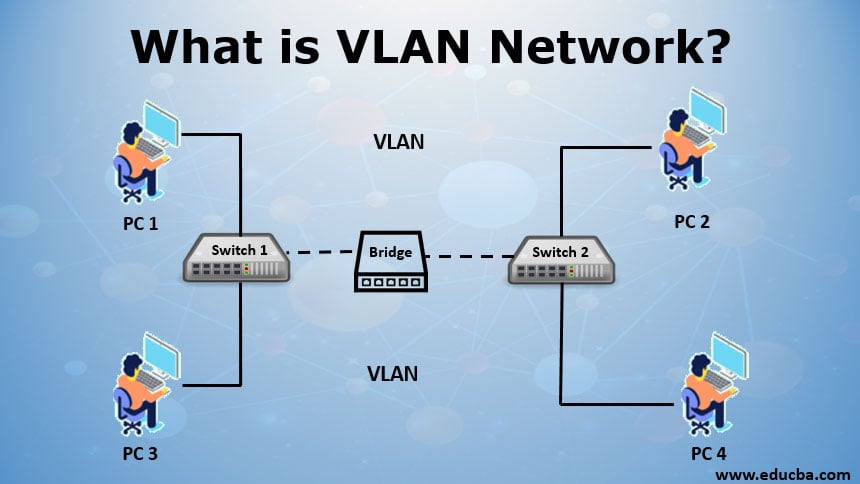
A virtual LAN (VLAN) is any broadcast domain that is partitioned and isolated in a computer network at the data link layer (OSI layer 2).[1][2]LAN is the abbreviation for local area network and in this context virtual refers to a physical object recreated and altered by additional logic. VLANs work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks. In this way, VLANs can keep network applications separate despite being connected to the same physical network, and without requiring multiple sets of cabling and networking devices to be deployed.
VLANs allow network administrators to group hosts together even if the hosts are not directly connected to the same network switch. Because VLAN membership can be configured through software, this can greatly simplify network design and deployment. Without VLANs, grouping hosts according to their resource needs the labor of relocating nodes or rewiring data links. VLANs allow devices that must be kept separate to share the cabling of a physical network and yet be prevented from directly interacting with one another. This managed sharing yields gains in simplicity, security, traffic management, and economy. For example, a VLAN can be used to separate traffic within a business based on individual users or groups of users or their roles (e.g. network administrators), or based on traffic characteristics (e.g. low-priority traffic prevented from impinging on the rest of the network's functioning). Many Internet hosting services use VLANs to separate customers' private zones from one other, allowing each customer's servers to be grouped in a single network segment no matter where the individual servers are located in the data center. Some precautions are needed to prevent traffic 'escaping' from a given VLAN, an exploit known as VLAN hopping.
To subdivide a network into VLANs, one configures network equipment. Simpler equipment might partition only each physical port (if even that), in which case each VLAN runs over a dedicated network cable. More sophisticated devices can mark frames through VLAN tagging, so that a single interconnect (trunk) may be used to transport data for multiple VLANs. Since VLANs share bandwidth, a VLAN trunk can use link aggregation, quality-of-service prioritization, or both to route data efficiently.
- VLAN identifier (VID) is a 12-bit field specifying the VLAN to which the frame belongs. The hexadecimal values of 0x000 and 0xFFF are reserved. All other values may be used as VLAN identifiers, allowing up to 4,094 VLANs.
- Virtual LAN (VLAN) Virtual LAN (VLAN) is a concept in which we can divide the devices logically on layer 2 (data link layer). Generally, layer 3 devices divides broadcast domain but broadcast domain can be divided by switches using the concept of VLAN. A broadcast domain is a network segment in which if a device broadcast a packet then all the.
- A VLAN, or virtual area network, is a subnetwork that groups together a collection of devices from different physical LANs. VLANs are often used on business computer networks.
Uses[edit]
VLANs address issues such as scalability, security, and network management. Network architects set up VLANs to provide network segmentation. Routers between VLANs filter broadcast traffic, enhance network security, perform address summarization, and mitigate network congestion.
A port is tagged for a VLAN when traffic that leaves the switch through that port has an IEEE 802.1Q header with that VLAN's numerical identifier (VLAN ID) on it. If a port is an untagged member of a VLAN, the switch removes the existing 802.1Q header before sending traffic through that port. A Virtual Local Area Network or VLAN is a way of partitioning computers on a network into cluster groups that serve a common business purpose. The LAN part indicates that we are partitioning physical hardware while the virtual part indicates we are using logic to accomplish it.
In a network utilizing broadcasts for service discovery, address assignment and resolution and other services, as the number of peers on a network grows, the frequency of broadcasts also increases. VLANs can help manage broadcast traffic by forming multiple broadcast domains. Breaking up a large network into smaller independent segments reduces the amount of broadcast traffic each network device and network segment has to bear. Switches may not bridge network traffic between VLANs, as doing so would violate the integrity of the VLAN broadcast domain.
VLANs can also help create multiple layer 3 networks on a single physical infrastructure. VLANs are data link layer (OSI layer 2) constructs, analogous to Internet Protocol (IP) subnets, which are network layer (OSI layer 3) constructs. In an environment employing VLANs, a one-to-one relationship often exists between VLANs and IP subnets, although it is possible to have multiple subnets on one VLAN.
Without VLAN capability, users are assigned to networks based on geography and are limited by physical topologies and distances. VLANs can logically group networks to decouple the users' network location from their physical location. By using VLANs, one can control traffic patterns and react quickly to employee or equipment relocations. VLANs provide the flexibility to adapt to changes in network requirements and allow for simplified administration.[2]
VLANs can be used to partition a local network into several distinctive segments, for instance:[3]
- Production
- Storage area network (SAN)
- Guest Internet access
- Demilitarized zone (DMZ)
A common infrastructure shared across VLAN trunks can provide a measure of security with great flexibility for a comparatively low cost. Quality of service schemes can optimize traffic on trunk links for real-time (e.g. VoIP) or low-latency requirements (e.g. SAN). However, VLANs as a security solution should be implemented with great care as they can be defeated unless implemented carefully.[4]
In cloud computing VLANs, IP addresses, and MAC addresses in the cloud are resources that end users can manage. To help mitigate security issues, placing cloud-based virtual machines on VLANs may be preferable to placing them directly on the Internet.[5]
Network technologies with VLAN capabilities include:[citation needed]
History[edit]
After successful experiments with voice over Ethernet from 1981 to 1984, W. David Sincoskie joined Bellcore and began addressing the problem of scaling up Ethernet networks. At 10 Mbit/s, Ethernet was faster than most alternatives at the time. However, Ethernet was a broadcast network and there was no good way of connecting multiple Ethernet networks together. This limited the total bandwidth of an Ethernet network to 10 Mbit/s and the maximum distance between nodes to a few hundred feet.
By contrast, although the existing telephone network's speed for individual connections was limited to 56 kbit/s (less than one hundredth of Ethernet's speed), the total bandwidth of that network was estimated at 1 Tbit/s[citation needed] (100,000 times greater than Ethernet).
Although it was possible to use IP routing to connect multiple Ethernet networks together, it was expensive and relatively slow. Sincoskie started looking for alternatives that required less processing per packet. In the process, he independently reinvented transparent bridging, the technique used in modern Ethernet switches.[6] However, using switches to connect multiple Ethernet networks in a fault-tolerant fashion requires redundant paths through that network, which in turn requires a spanning tree configuration. This ensures that there is only one active path from any source node to any destination on the network. This causes centrally located switches to become bottlenecks, limiting scalability as more networks are interconnected.
To help alleviate this problem, Sincoskie invented VLANs by adding a tag to each Ethernet frame. These tags could be thought of as colors, say red, green, or blue. In this scheme, each switch could be assigned to handle frames of a single color, and ignore the rest. The networks could be interconnected with three spanning trees, one for each color. By sending a mix of different frame colors, the aggregate bandwidth could be improved. Sincoskie referred to this as a multitree bridge. He and Chase Cotton created and refined the algorithms necessary to make the system feasible.[7] This color is what is now known in the Ethernet frame as the IEEE 802.1Q header, or the VLAN tag. While VLANs are commonly used in modern Ethernet networks, they are not used in the manner first envisioned here.
In 1998, Ethernet VLANs were described in the first edition of the IEEE 802.1Q-1998 standard.[8] This was extended with IEEE 802.1ad to allow nested VLAN tags in service of provider bridging. This mechanism was improved with IEEE 802.1ah-2008.
Configuration and design considerations[edit]
Early network designers often segmented physical LANs with the aim of reducing the size of the Ethernet collision domain—thus improving performance. When Ethernet switches made this a non-issue (because each switch port is a collision domain), attention turned to reducing the size of the data link layer broadcast domain. VLANs were first employed to separate several broadcast domains across one physical medium. A VLAN can also serve to restrict access to network resources without regard to physical topology of the network.[a]
VLANs operate at the data link layer of the OSI model. Administrators often configure a VLAN to map directly to an IP network, or subnet, which gives the appearance of involving the network layer. Generally, VLANs within the same organization will be assigned different non-overlapping network address ranges. This is not a requirement of VLANs. There is no issue with separate VLANs using identical overlapping address ranges (e.g. two VLANs each use the private network192.168.0.0/16). However, it is not possible to route data between two networks with overlapping addresses without delicate IP remapping, so if the goal of VLANs is segmentation of a larger overall organizational network, non-overlapping addresses must be used in each separate VLAN.
A basic switch that is not configured for VLANs has VLAN functionality disabled or permanently enabled with a default VLAN that contains all ports on the device as members.[2] The default VLAN typically uses VLAN identifier 1. Every device connected to one of its ports can send packets to any of the others. Separating ports by VLAN groups separates their traffic very much like connecting each group using a distinct switch for each group.
Remote management of the switch requires that the administrative functions be associated with one or more of the configured VLANs.
In the context of VLANs, the term trunk denotes a network link carrying multiple VLANs, which are identified by labels (or tags) inserted into their packets. Such trunks must run between tagged ports of VLAN-aware devices, so they are often switch-to-switch or switch-to-router links rather than links to hosts. (Note that the term 'trunk' is also used for what Cisco calls 'channels' : Link Aggregation or Port Trunking). A router (Layer 3 device) serves as the backbone for network traffic going across different VLANs. It is only when the VLAN port group is to extend to another device that tagging is used. Since communications between ports on two different switches travel via the uplink ports of each switch involved, every VLAN containing such ports must also contain the uplink port of each switch involved, and traffic through these ports must be tagged.
Switches typically have no built-in method to indicate VLAN to port associations to someone working in a wiring closet. It is necessary for a technician to either have administrative access to the device to view its configuration, or for VLAN port assignment charts or diagrams to be kept next to the switches in each wiring closet.
Protocols and design[edit]
The protocol most commonly used today to support VLANs is IEEE 802.1Q. The IEEE 802.1 working group defined this method of multiplexing VLANs in an effort to provide multivendor VLAN support. Prior to the introduction of the 802.1Q standard, several proprietary protocols existed, such as Cisco Inter-Switch Link (ISL) and 3Com's Virtual LAN Trunk (VLT). Cisco also implemented VLANs over FDDI by carrying VLAN information in an IEEE 802.10 frame header, contrary to the purpose of the IEEE 802.10 standard.
Both ISL and IEEE 802.1Q tagging perform explicit tagging – the frame itself is tagged with VLAN information. ISL uses an external tagging process that does not modify the Ethernet frame, while 802.1Q uses a frame-internal field for tagging, and therefore does modify the basic Ethernet frame structure. This internal tagging allows IEEE 802.1Q to work on both access and trunk links using standard Ethernet hardware.
IEEE 802.1Q[edit]
Under IEEE 802.1Q, the maximum number of VLANs on a given Ethernet network is 4,094 (4,096 values provided by the 12-bit VID field minus reserved values at each end of the range, 0 and 4,095). This does not impose the same limit on the number of IP subnets in such a network since a single VLAN can contain multiple IP subnets. IEEE 802.1ad extends the number of VLANs supported by adding support for multiple, nested VLAN tags. IEEE 802.1aq (Shortest Path Bridging) expands the VLAN limit to 16 million. Both improvements have been incorporated into the IEEE 802.1Q standard.
Cisco Inter-Switch Link[edit]
Inter-Switch Link (ISL) is a Cisco proprietary protocol used to interconnect switches and maintain VLAN information as traffic travels between switches on trunk links. ISL is provided as an alternative to IEEE 802.1Q. ISL is available only on some Cisco equipment and has been deprecated.[10]
Cisco VLAN Trunking Protocol[edit]
VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that propagates the definition of VLANs on the whole local area network. VTP is available on most of the Cisco Catalyst Family products. The comparable IEEE standard in use by other manufacturers is GARP VLAN Registration Protocol (GVRP) or the more recent Multiple VLAN Registration Protocol (MVRP).
Multiple VLAN Registration Protocol[edit]
Multiple VLAN Registration Protocol is an application of Multiple Registration Protocol that allows automatic configuration of VLAN information on network switches. Specifically, it provides a method to dynamically share VLAN information and configure the needed VLANs.
Vlan 1006
Membership[edit]
VLAN membership can be established either statically or dynamically.
Static VLANs are also referred to as port-based VLANs. Static VLAN assignments are created by assigning ports to a VLAN. As a device enters the network, the device automatically assumes the VLAN of the port. If the user changes ports and needs access to the same VLAN, the network administrator must manually make a port-to-VLAN assignment for the new connection.
Dynamic VLANs are created using software or by protocol. With a VLAN Management Policy Server (VMPS), an administrator can assign switch ports to VLANs dynamically based on information such as the source MAC address of the device connected to the port or the username used to log onto that device. As a device enters the network, the switch queries a database for the VLAN membership of the port that device is connected to. Protocol methods include Multiple VLAN Registration Protocol (MVRP) and the somewhat obsolete GARP VLAN Registration Protocol (GVRP).
Protocol-based VLANs[edit]
In a switch that supports protocol-based VLANs, traffic may be handled on the basis of its protocol. Essentially, this segregates or forwards traffic from a port depending on the particular protocol of that traffic; traffic of any other protocol is not forwarded on the port. This allows, for example, IP and IPX traffic to be automatically segregated by the network.
VLAN cross connect[edit]
VLAN cross connect (CC or VLAN-XC) is a mechanism used to create Switched VLANs, VLAN CC uses IEEE 802.1ad frames where the S Tag is used as a Label as in MPLS. IEEE approves the use of such a mechanism in part 6.11 of IEEE 802.1ad-2005.
See also[edit]
- HVLAN, hierarchical VLAN
- Multiple VLAN Registration Protocol, GARP VLAN Registration Protocol
- Virtual Extensible LAN (VXLAN)
Notes[edit]
- ^The strength of VLAN security can be compromised by VLAN hopping. VLAN hopping can be mitigated with proper switchport configuration.[9]
References[edit]
- ^IEEE 802.1Q-2011, 1. Overview
- ^ abcIEEE 802.1Q-2011, 1.4 VLAN aims and benefits
- ^'VLAN & Its Implementation over ATM by using IP: a communication'(PDF). Discovery Institute. Archived from the original(PDF) on 2015-06-18.
- ^'Virtual LAN Security: weaknesses and countermeasures', SANS Institute InfoSec Reading Room, SANS Institute, retrieved 2018-05-18
- ^Amies A; Wu C F; Wang G C; Criveti M (21 June 2012), 'Networking on the cloud'(PDF), IBM developerWorks, archived from the original(PDF) on 2013-11-01
- ^Sincoskie, WD (2002) 'Broadband packet switching: a personal perspective.' IEEE Commun 40: 54-66
- ^W. D. Sincoskie and C. J. Cotton, 'Extended Bridge Algorithms for Large Networks' IEEE Network, Jan. 1988.
- ^IEEE Std. 802.1Q-1998, Virtual Bridged Local Area Networks. 1998.
- ^Rik Farrow. 'VLAN Insecurity'. Archived from the original on 2014-04-21.
- ^CCNA Exploration LAN Switching and Wireless course, v 4.0, sec 3.2.3
Further reading[edit]
- Andrew S. Tanenbaum, 2003, 'Computer Networks', Pearson Education International, New Jersey.
Introduction
In previous chapters, we learnt how VLANs segment broadcast traffic on a switch and segment a switched network into different LANs, we also learnt how VLAN information can be transmitted to other switches in the network using VTP and how we can avoid layer two loops using STP.
Consider, this, as the network administrator, one of your tasks is to create and assign different users to VLANs in your network, you have three main departments which should be logically segmented using VLANs, VLAN 10 – FINANCE, VLAN 20 – SALES and VLAN 30 – HR.
The use of VLANs means that users would not be able to communicate across departments, i.e. a user in FINANCE, would not be able to send a message to a user in SALES since they are on different broadcast domains.
In many enterprises, you will find that information sharing across departments is a requirement, therefore, the question begs, how do you make users in the SALES and FINANCE department communicate, yet they are on different VLANS?
In this chapter, we will discuss the role played by inter-VLAN routing in communication between different VLANs. We will learn how it works, consider the various methods that can be used to implement it, configure inter-VLAN routing using router-on-a-stick and traditional inter-VLAN routing, compare the two styles of implementation and finally verify and troubleshoot inter-VLAN routing.
Introduction to inter-vlan routing
When we learnt about VLANs, we said that each VLAN is usually on its own subnet, switches mainly operate at layer 2 of the OSI model and therefore they do not examine the logical addresses. Therefore, user nodes located on different VLANs cannot communicate by default. In many cases, we may need connectivity between users located on different VLANs. The way this can be accomplished is through inter-VLAN routing.
In this course, we will look at one type of inter-VLAN routing, which is through the use of a router.
Definition
Inter-VLAN routing can be defined as a way to forward traffic between different VLAN by implementing a router in the network. As we learnt previously, VLANs logically segment the switch into different subnets, when a router is connected to the switch, an administrator can configure the router to forward the traffic between the various VLANs configured on the switch. The user nodes in the VLANs forwards traffic to the router which then forwards the traffic to the destination network regardless of the VLAN configured on the switch.
The figure below, shows how this process works.
Information destined for PC B, leaves PC A with the VLAN 20 tag, when it gets to R1, the router, changes the format of this message from VLAN 20, to VLAN 30, it then sends it back to the switch and the switch finally sends the message to its intended recipient PC B.
There are two ways in which inter-VLAN routing can be accomplished.
- Traditional inter-VLAN routing
- Router-on-a-stick
Traditional inter-VLAN routing
In this type of inter-VLAN routing, a router is usually connected to the switch using multiple interfaces. One for each VLAN. The interfaces on the router are configured as the default gateways for the VLANs configured on the switch.
The ports that connect to the router from the switch are configured in access mode in their corresponding VLANs.
When a user node sends a message to a user connected to a different VLAN, the message moves from their node to the access port that connects to the router on their VLAN. When the router receives the packet, it examines the packet's destination IP address and forwards it to the correct network using the access port for the destination VLAN. The switch now can forward the frame to the destination node since the router changed the VLAN information from the source VLAN to the destination VLAN.
In this form of inter-VLAN routing, the router has to have as many LAN interfaces as the number of VLANs configured on the switch. Therefore, if a switch has 10 VLANs, the router should have the same number of LAN interfaces.
Take the scenario shown below.
If PC A in VLAN 20, wanted to send a message to PC B in VLAN 30, the steps it would take are shown below.
- PC A would check whether the destination IPv4 address is in its VLAN if it is not, it would need to forward the traffic to its default gateway which is the ip address on Fa0/0 on R1.
- PC A then sends an ARP request to AS1 so as to determine the physical address of Fa0/0 on R1. Once the router replies, PC A can send the frame to the router as a unicast message, since AS1 has Fa0/0's MAC address, it can forward the frame directly to R1.
- When the router receives the frame, it compares the destination IP address by referring to its routing table so as to know to which interface it should send the data towards the destination node.
- The router then sends an ARP request out the interface connected to the destination VLAN in this case out Fa0/1, when the switch receives the message, it would flood it to its ports and in this case, PC B would reply with its MAC address.
- R1 would then use this information to frame the packet and finally send it to PC B as a unicast frame.
Configuring traditional inter-VLAN routing
In this section, we will configure Inter-VLAN routing on the router and the switch using the scenario we have just seen above. All the VLANs are active and the PCs have been assigned ports, our configuration will only be limited to the router's inter-VLAN configuration and the switch ports connecting to R1.
The ip addressing in use is shown below.
Testing connectivity using the ping command should reveal that PC A cannot ping PC B.
The first step is to configure the switchports to access the specified VLAN, fa0/1 to VLAN 20 and fa0/2 to VLAN 30. This is accomplished using the commands shown below.
This is the only configuration on the switch, once this is done save the configuration and move on to the router.
On R1, we need to configure its interfaces with the default gateways corresponding to the VLANs. That is; on fa0/0 -192.168.20.1/24 and on fa0/1 – 192.168.30.1/24. We accomplish this using the commands shown below.
With this configuration we should save and test for connectivity on PC A and PC B, by using the ping command, and the results should be successful. Examining the routing table of R1 should show us the two routes as shown in the output below. This confirms that the router knows of the two VLANs and therefore traffic can flow between them.
Inter-VLAN routing using router-on-a-stick
With the example shown above, there are several concerns, suppose we had 10 or even 20 VLANs configured on the switch, even if the switch has enough ports to support the connection to the router, it is highly unlikely that the router would have so many Ethernet interfaces. Therefore we need a way to use the limited router interfaces to support routing between many VLANs that may be on a switch.
Introduction to Router-on-a-stick
In the second type of inter-VLAN routing which is Router-on-a-stick, the router is connected to the switch using a single interface. The switchport connecting to the router is configured as a trunk link. The single interface on the router is then configured with multiple IP addresses that correspond to the VLANs on the switch. This interface accepts traffic from all the VLANs and determines the destination network based on the source and destination IP in the packets. It then forwards the data to the switch with the correct VLAN information.
As you can see in the diagram below, the router is connected to the switch AS1 using a single, physical network connection.
In this type of inter-VLAN routing, the interface connecting the router to the switch is usually a trunk link. The router accepts traffic that is tagged from the VLANs on the switch through the trunk link. On the router, the physical interface is divided into smaller interfaces called subinterfaces. When the router receives the tagged traffic, it forwards the traffic out to the subinterface that has the destination IP address.
subinterfaces aren't real interfaces but they use the LAN physical interfaces on the router to forward data to various VLANs. Each subinterface is configured with an IP address and assigned a VLAN based on the design.
Configuring inter-VLAN routing using router-on-a-stick
In this section, we will configure inter-VLAN routing using router-on-a-stick and using the topology shown below. It has been modified by adding additional VLANs so as to show the effectiveness of using router-on-a-stick as opposed to traditional inter-VLAN routing.
In our scenario, we have four hosts located on 4 VLANs, the native VLAN is VLAN 99. Our task is to configure inter-VLAN routing on the router and the switch and ensure that all devices can communicate at the end of the lab. The Ip addressing scheme for the topology is shown below.
NOTE: Unlike traditional inter-VLAN routing, when using subinterfaces, we do not assign an ip address to the interface on the router that is connected to the switch.
In this lab, the configuration on the PC's and the switch ports connecting to them is done correctly, our task is to configure the interface fa0/1 on AS1 and configuration on R1.
Step 1.
On switch AS1 we need to define the interface connected to the router as a trunk link. This will allow traffic from all VLANs to get to the router using that interface. The command to accomplish this is on AS1 is:
NOTE: many errors may rise if the switchport connected to the switch is not configured as a trunk.
Step 2.
At this step inter-VLAN routing can be configured on the router. As we mentioned earlier, when configuring router-on-a-stick, we use subinterfaces.
Each subinterface is created using the interface interface_id.Subinterface_id in the global configuration mode. As shown below.
NOTE: the '.' Between the interface ID and the subinterface ID is a must. The subinterface ID is a logical number but ideally it should describe the VLAN ID.
To create a subinterface which will be used to route for VLAN 10, we will use the command shown below.
This will take us into the subinterface configuration mode which is denoted by the prompt shown below.
In the subinterface mode, we can link the VLAN ID to this interface as well as assign it an ip address and a subnet mask.
Sniper 3 ghost warrior ps4 cheats. Step 3.
To link the subinterface with the specific VLAN, we use the command 'encapsulation dot1q ' this will specify that this interface will get traffic from the specified VLAN. In our example, the command needed to link VLAN 10 to this subinterface is shown below:
Step 4.
In this mode, we can also assign the subinterface with the ip address and subnet mask which will be used for VLAN 10. The default gateway on the PC's will be used as the interface address as shown below.
Step 5.
When all the subinterfaces have been assigned to their respective VLANs, we need to activate the LAN interfaces that they are connected to by issuing the no shutdown command.
This will activate the interface and allow for inter-VLAN routing.
NOTE: the native VLAN is used to carry untagged traffic, the configuration for the native VLAN subinterface on the router is done using the command shown below.
The native keyword is used to identify the specified VLAN as the native VLAN.
Vlan Id
In our scenario, the commands needed to configure inter-VLAN routing using router-on-a-stick are shown below.
With this configuration, we should be able to communicate between the different VLANs. The output of the show ip route command should confirm that we are connected to all four routes as shown in the output below. Running the ping command should give us replies for all routes in the routing table.
Comparison of router-on-a-stick and traditional inter-VLAN routing
In this table, we have compared router-on-a-stick and traditional inter-VLAN routing.
NOTE: in the CCNA exams, understanding inter-VLAN routing is very important, the focus is mainly on router-on-a-stick inter-VLAN routing, however, you should not ignore the traditional inter-VLAN routing.
Verifying and troubleshooting inter-VLAN routing issues
In this section, we will try to understand some of the common problems associated with inter-VLAN routing using router-on-a-stick configuration.
In verifying inter-VLAN routing, the commands mostly used are:
- Show run
- Show ip interface brief
- Show interface
The output of the show interface should give you output similar to what is shown in the output below.
From the output above, the VLAN ID, the encapsulation, and the status can be verified using this command. The section highlighted in red shows the encapsulation type and VLAN ID.
Most of the errors that you may encounter when dealing with inter-VLAN routing are misconfiguration errors in the subinterfaces. However, by using the step by step guide shown and the verification and troubleshooting commands you can be able to quickly resolve any issues.
Summary
In this chapter, we have looked at how we can make users located on different VLANs communicate, we have looked at traditional inter-VLAN routing as well as inter-VLAN routing using router-on-a-stick. We also compared the two methods and configured them.
For the most part of this course, we have been primarily focused on LAN technologies, many enterprises span over large geographical distances. In the next few chapters, we will discuss WAN technologies and understand how they work.

